Waiting for presentation
* * *
--:--:--
보안. 어떤 느낌인가요?
How does feel for "security"?
Why is security difficult?
Results of a Survey on Information Security Awareness of Office Workers
2017, ITWORLD and Fuji Xerox Korea.
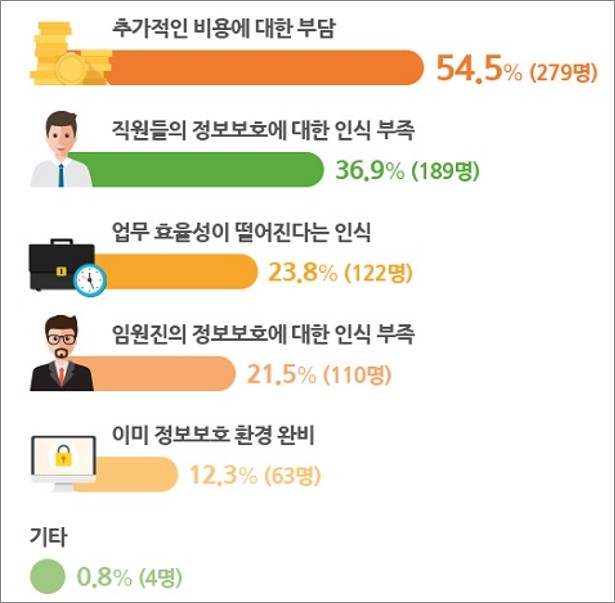
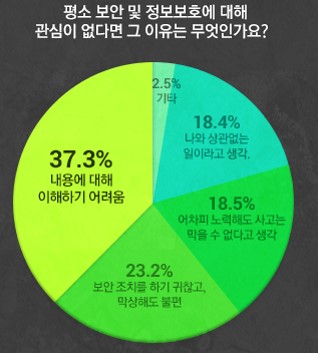
Why aren't you interested
in protecting information?
It's hard.
It's better to use an outside company.
It has nothing to do with me.
해커. 어떤 느낌인가요?
How does feel for "Hacker"?



So, What is the vulnerability?
- Faults A flaw in the system. (bug)
- Accessibility Attacker access to faults.
- Exploitable Possible exploit for an attacker to a fault.
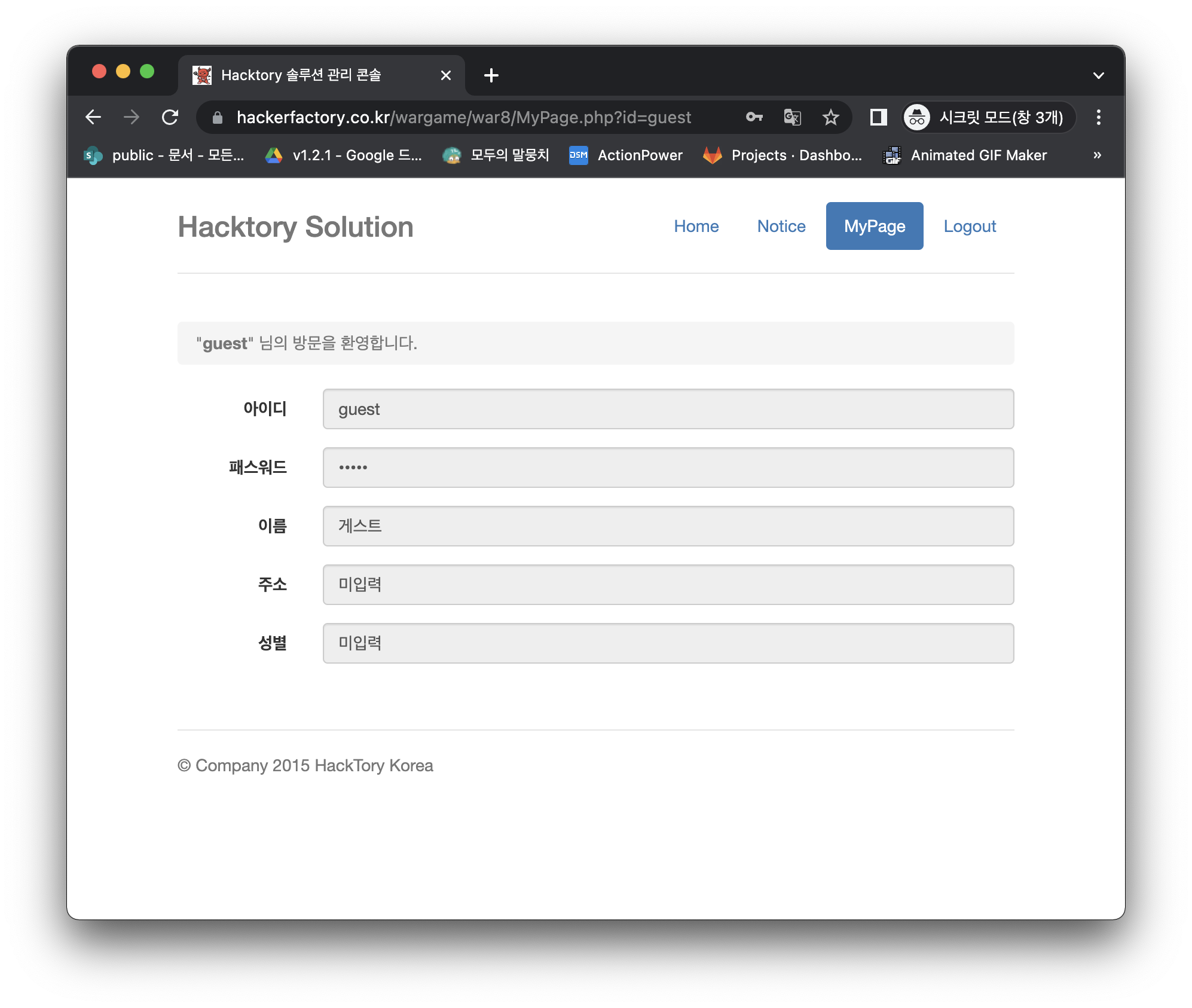
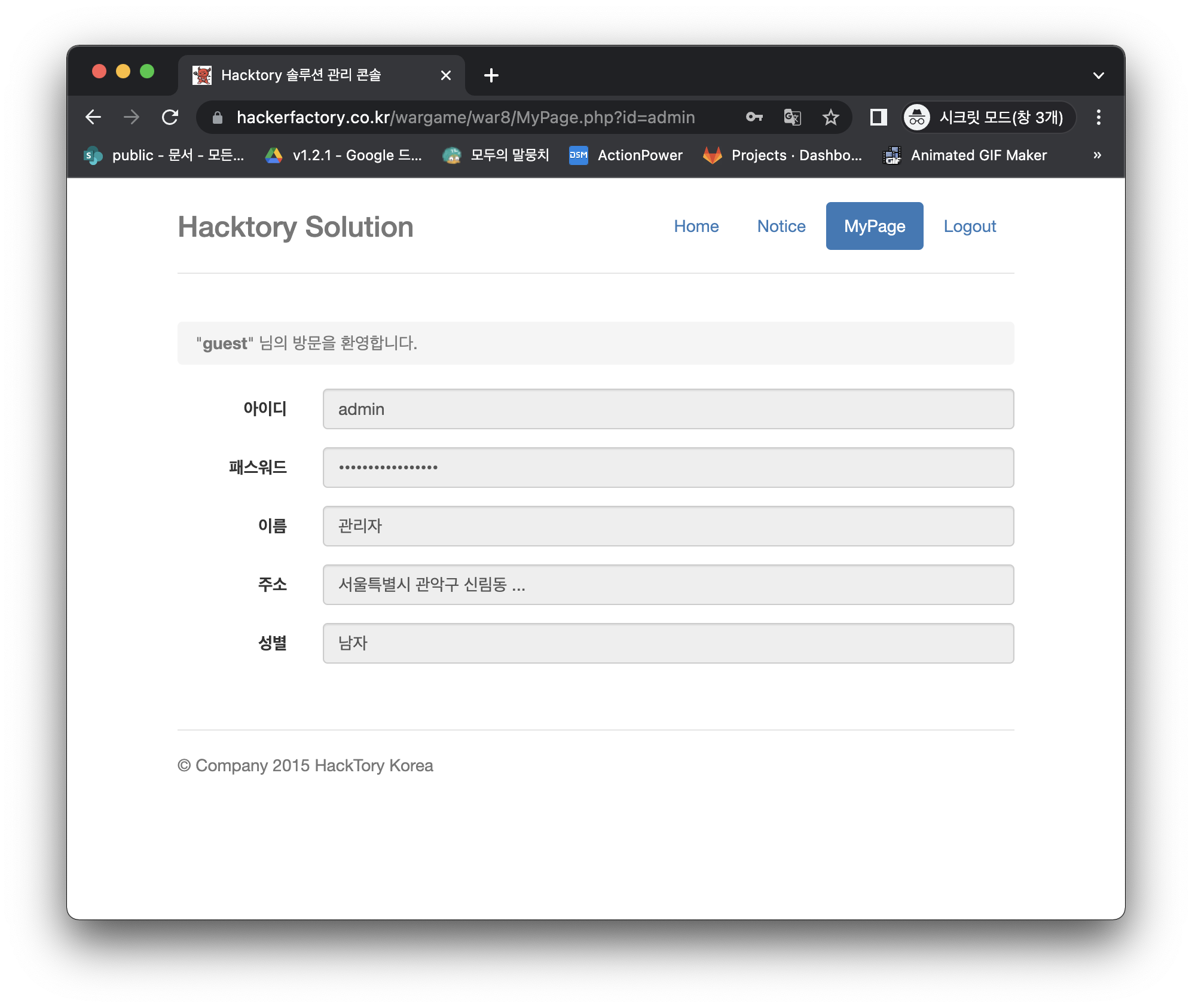
We're gonna make a bulletin board system.
- 1. we support font style, so we used innerHTML.
- 2. we filter <script> tag. for prevent XSS attack.
- 3. This bulletin board can be used by anyone.
<a href="javascript:eval(`alert('hello world');`)">test</a>
How to find the Vulnerability?
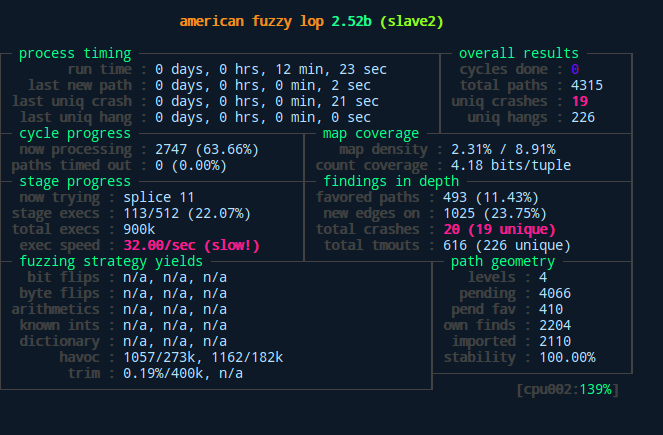
- 1. Using Automated Vulnerability Detection Tools. (Fuzzing)
- 2. Check for unexceptional code
- 3. Find exploit payload (using BOF, UAF, ROP)
Choi Subong
A01
Broken Access
Control
Access Control
Access control is the ability to create and execute policies to prevent users from acting beyond their rights.
Broken Access Control
When access control is weakly implemented, users can go beyond their given privileges and unauthorized access to unauthorized data, manipulate or delete it.
Example
Who grant permissions to all users by default that should only be granted to specific users.
Who can log in as a user and act as an administrator if an unauthenticated user can force browsing pages that require authentication.
Access control for POST, PUT, DELETE API requests is missing.
Who can manipulate requests such as parameters or cookies to raise permissions or use other users' permissions.
A02
Cryptographics
Failures
Existing sensitive data exposure renamed encryption failure. This topic covers a wide range of general topics related to encryption.
Errors or deficiencies in encryption lead to sensitive data exposure.
Maybe use a vulnerable version of encryption technology, or you may have insufficient key management.
Example
Hard-coding encryption keys to source code
Without salt or key stretching
A03
Injection

A04
Insecure
Design
A05
Security
Misconfiguration
TL;DR
Keep the setting to a minimum. Turn off everything you don't need, or the thief will use it later.
Check this components
Unnecessary ports, unnecessary pages, unnecessary accounts/authorities, missing security header settings, missing various OS, frameworks, libraries, database security settings
A06
Vulnerable and
Outdated Components
Don't overstretch your dependency.
Be careful when introducing all components.
In addition, you must maintain a minimum of components.
If it's something we can do easily, consider without a library.
These external component may be convenient immediately, but it may not be good for maintenance in the long run.
Prevent
Remove unnecessary software
Check all software versions you use with geometry management
Establish a patch management process to keep up to date with software
Continuously monitor known vulnerabilities to identify vulnerable software usage
A07
Identification and
Authentication Failures
Integration and Renamed
Broken Authentication + Identification failures, Items that correspond to user identity authentication and authentication and session management
Example
Exposed to Credential Stuffing, Brute Forcing attacks, etc. due to the absence of multi-factor authentication or secondary authentication
Unrestricted authentication failure and exposed to brute force attack
There is no secure password generation policy, allowing vulnerable password generation
If the URL exposes the authentication session ID (GET Method)
After logging in, you reuse an existing session ID without issuing it with a new session ID
There is no session timeout or no session destruction after logout
Prevent
Implement multi-factor or secondary certification.
Apply secure password generation policy and limit on number of authentication failures.
Create a new session ID at login and send the authentication session through the header on the encrypted channel.
Establishing Session Destruction and Expiration Policies.
A08
Software and Data
Integrity Failures
Detail
Software and data integrity errors occur when applications rely on untrusted sources, storage, and CDNs, plugins, libraries, and modules.
You must add an integrity verification procedure for the code used by the application.
Example
Modulation is possible because there is no integrity verification for the library or module used by the application
If there is no validation for the update supply chain
If there is no proper security review for the CI/CD pipeline
Without integrity verification for serialized data
Prevent
Validate application integrity using electronic signatures, hash algorithms, etc
Ensure that your library is using a trusted repository, and if it is an important service, specify and use a separate internal repository
Conduct regular security reviews for CI/CD pipelines
Perform integrity verification on serialized data when using serialized/de-serialized libraries
A09
Security Logging and
Monitoring Failures
Example
There is no logging for important functions such as login, authentication failure, permission settings, etc.
If there is no backup procedure for the log at regular intervals.
When logging and monitoring are not clearly identified and logging is not performed.
Prevent
Log all logins, access controls, authentication failures and keep them as regular backups.
Ensure logging is created in the appropriate format to leverage log management solutions, etc.
Set and monitor thresholds to detect and respond quickly to suspicious activity.
Establish a plan to respond to and recover from an infringement.
A10
SSRF; Server-side
Request Forgery
Example
Allow servers to access local or remote resources without proper verification procedures.
Prevent
Applying access control rules through firewalls even when communicating with the internal networks to which the server belongs.
Validation of all user-supplied data.
Validate server-side performance results for user requests.
Conclusion
Doubt it
Do NOT TRUST client.
Careful filtering
Always verify the input carefully.
especially if there is any room for user intervention in input values such as exec, child_process, sql, and file search, you should do your best to filter and write test cases, and find exception cases diligently.
Trust framework
If my code is blocked by framework, there is a high probability that the code I am trying to squeeze is extremely dangerous.
All frameworks have security recommendations. Be sure to read the document.
Why did Starcraft become a masterpiece?
OWASP - CheatSheet
Please refer to the cheat sheet when you are concerned about security.
OWASP has documented it to advise most cases.
It's well organized and deep.
Even if it's not now, please read the relevant information before you design something.
의심하는 습관 들이기
Let's Play DOUBT Game!
Thank you!
any question?